The two virtual machines you will be installing are configured as follows.
Please note that the Oracle VirtualBox machines are for testing and education purposes only, as such are unsupported and should not to be used in production environment. The machines contain no firewall and selinux has been disabled.
Memory
Each virtual machine is configured by default with 2.3 Gb of memory, which is the minimum required.
If you are installing Rep Attack on a host machine with more than 6Gb of memory, you can increase the virtual machine's performance by increasing the --memory parameter for each machine in the machine_setup script prior to executing it.
The recommended value for each VM is 2.3 Gb or 1/3 of the physical memory of the host, up to a maximum of 4 Gb. For example, if you have a host machine with 8 Gb of memory, then 2730 Mb would be appropriate.
Note that the maximum amount of memory that an Oracle XE 11g database uses cannot exceed 1 Gb, even if more is available. The other memory is configured for non-Oracle operating system processes.
CPU
Most modern computers, even laptops, have multi-core CPUs. Each virtual machine is configured by default with 2 virtual CPUs. Oracle XE 11g will consume, at most, the processing resources equivalent to one CPU. The other CPU is configured for other, non-Oracle operating system processes.
Disk
Each machine has one 30 Gb disk. The disk is configured as a dynamic VirtualBox disk and only consumes the space required by it's contents. The initial contents of the disks take up about 12 Gb of space but the disk can grow up to 30 Gb if required.
Audio
No audio device has been configured for the virtual machines.
Network Adapters
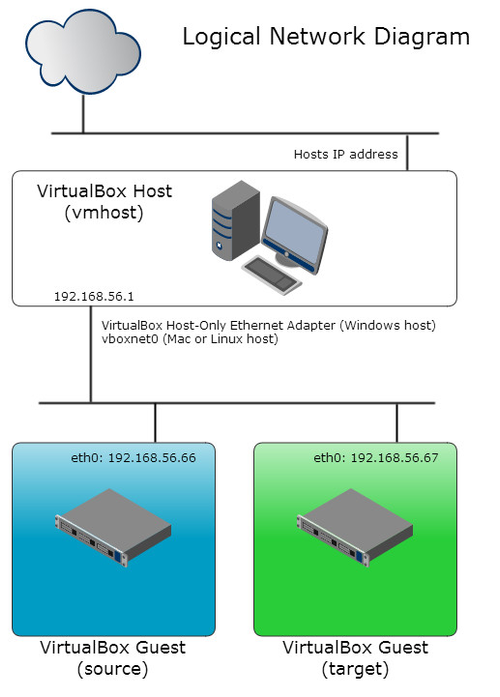
Each virtual machine has a single Host-only network adapter configured on the default Host-only network of 192.168.56.0/24.
The Host-only network is a VirtualBox network that is internal to the host computer. Only the host computer and the virtual machines on the same Host-only network are connected to each other.
The Host-only network used by Rep Attack on your host machine requires no resources from the host's network. It is only connected to your host machine and not to the wider network so all traffic between the virtual machines will remain on your host and the machines have no direct connection to the Internet.
The source and target machines have hard coded IP addresses of 192.168.56.66 and 192.168.56.67 respectively.
If you already have VirtualBox installed and you are using the default Host-only network and you have existing machines running on these addresses, then you will have to shut down those machines while the Rep Attack machines are running, or change the IP addresses of the Rep Attack machines.
The Host-only network will enable you to use client tools on your host machine to connect to the databases on the virtual machines. So you can use tools like SQL*Developer or TOAD etc on your host.
Serial Ports
No serial ports have been configured for the virtual machines.
USB Ports
Each machine has been configured with 1.0 USB controller although this is not used as part of the Rep Attack. A USB 2.0 controller has not been configured as this requires the installation of the Oracle specific extensions to VirtualBox.
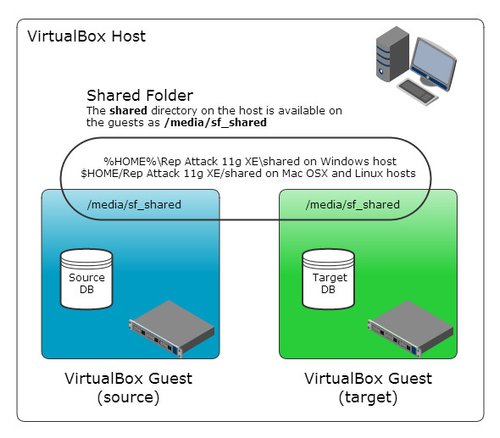
Shared Folders
A common shared folder has been configured on each virtual machine. These are used to transfer files to and from the virtual machines from the host.
The virtual machines are not connected to the internet so if you want to download something, use the internet connection on the host and place the file in the shared directory.
Snapshots
The virtual machines execute from an 'Initial" snapshot that allows you to restore the machines back to their original starting position.
Snapshots are a great way to revert a machine back to a known configuration so you can start again, but remember, ANY changes you've made since the snaphot was taken will be lost.
If you have created any scripts or files on your virtual machines you want to keep, make sure you put a copy of them in the shared folder (/media/sf_shared) as this belongs to the host machine and it's contents will be saved when the snapshot is restored.
Stopping, Starting, Restoring, and Removing the Machines
The machines are started automatically via the machine_setup script when you create them for the first time but after that you are on your own to look after them. Here's a few pointers to administer your Rep Attack environment.
Stopping
Log out of any terminal sessions, then on the console, as root (password is root) issue the shutdown -h now command. This should perform an orderly shutdown of the database and machine.
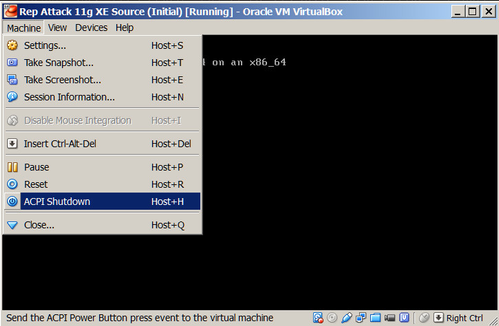
Shutdown for the lazy
The Rep Attack machines have been configured with the Advanced Configuration and Power Interface (ACPI) daemon running. This daemon will perform an orderly shutdown using the shutdown -h now command if it detects the (virtual) power button is pressed. You can press the virtual power button by selecting the ACPI Shutdown from the Machine menu on the machines console window.
0 Comments